The Executive's AML Compliance Checklist: A Data-Driven Framework for 2025
Brian's Banking Blog
In an era of escalating regulatory scrutiny and sophisticated financial crime, a static AML compliance checklist is a liability. For bank executives and directors, the mandate is clear: architect a dynamic, data-informed defense system that not only satisfies examiners but actively protects the institution's integrity and financial stability. This requires a cultural shift from 'check-the-box' compliance to proactive risk management, where every component of your AML program is measurable, defensible, and benchmarked against peer performance.
This framework provides a strategic AML compliance checklist designed to fortify your institution. Each pillar is analyzed through the lens of data intelligence, demonstrating how a platform like Visbanking transforms regulatory burdens into strategic advantages. We will explore how robust data analytics not only strengthens controls but also provides the board with the clarity needed to make confident, forward-looking decisions in a complex risk environment. These are the seven core pillars that define a modern, resilient AML program.
1. Pillar 1: Fortifying Your Customer Due Diligence (CDD) Program
Your Customer Due Diligence (CDD) program is the bedrock of your entire AML framework. For executives, the critical question is not merely “Do we have a CDD program?” but “How effective and efficient is our CDD program compared to our peers?” An underperforming program introduces unacceptable risk and creates operational drag that directly impacts the bottom line.
If your average customer onboarding time is ten days while industry leaders average four, you are losing valuable business due to compliance friction. This is where data intelligence becomes indispensable. Benchmarking key metrics—such as documentation exception rates and the frequency of high-risk customer reviews—against a curated peer group transforms abstract risk into a concrete performance gap. This data-driven insight allows you to quantify the cost of inefficiency and justify strategic investments in technology or process redesign.
Actionable Strategy: Data-Driven Optimization
A robust CDD program is not a static document; it is a dynamic, risk-based system. The objective is to allocate your most intensive resources to the highest-risk profiles while streamlining the process for low-risk customers. For instance, following major regulatory settlements, institutions like HSBC implemented enhanced due diligence (EDD) programs, demonstrating a commitment to rectifying past failures by applying stricter scrutiny where it was most needed.
To achieve this, your team must execute these critical actions:
- Implement a Risk-Based Approach: Tier customers based on factors like geographic location, transaction patterns, and business type. This allows you to apply EDD to high-risk clients without overburdening every new account with unnecessary friction.
- Automate Verification: Leverage automated tools for identity and document verification to reduce manual errors and accelerate onboarding for standard-risk customers.
- Establish Clear Escalation Procedures: Ensure frontline staff know precisely when and how to escalate a high-risk case to senior compliance officers, preventing bottlenecks and ensuring expert review.
Benchmarking Key Performance Indicators
Tracking the right metrics provides a clear view of your program's health. The following infographic highlights target KPIs for a high-performing CDD function.
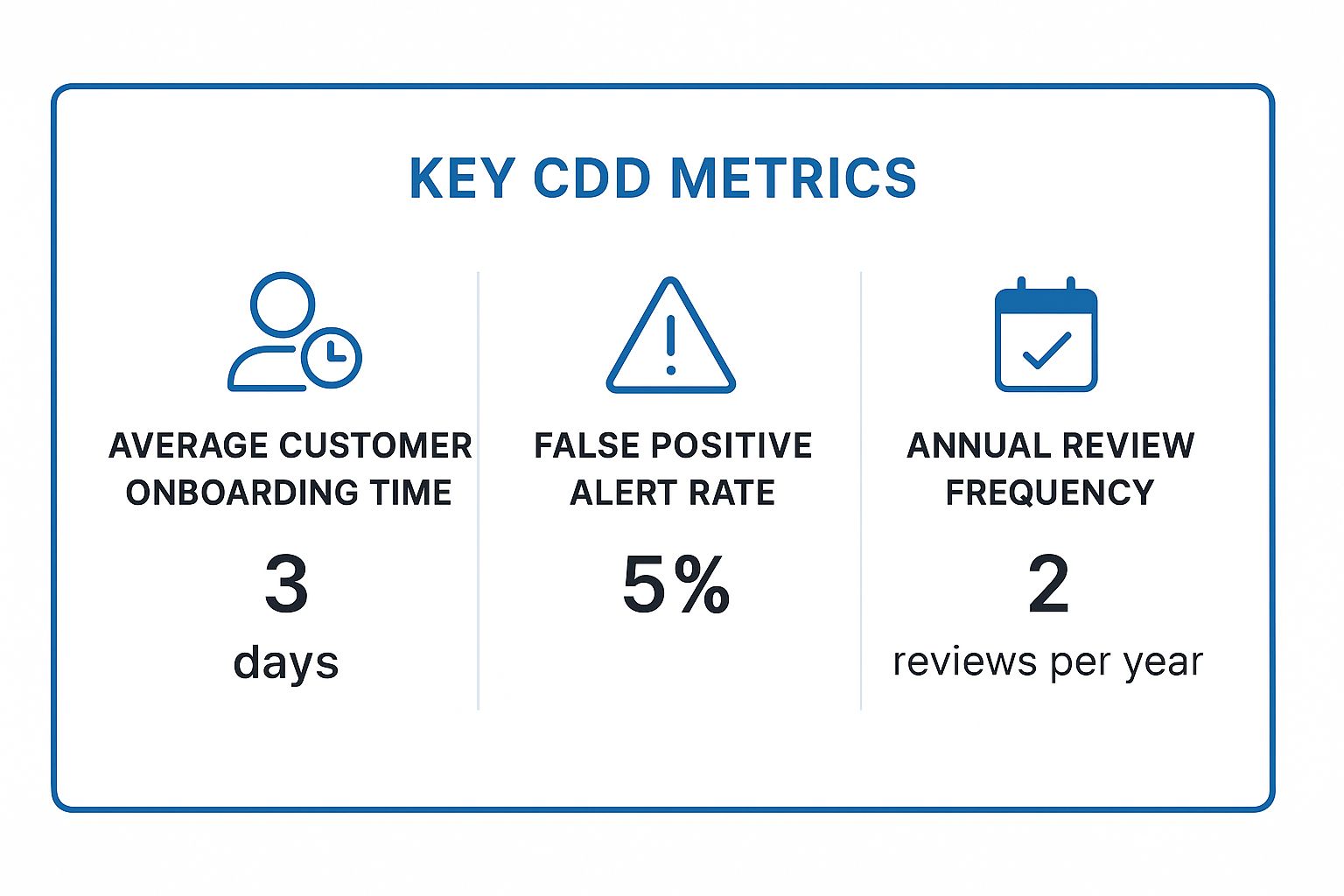
These figures represent an efficient, well-tuned system where automation and risk-based strategies minimize friction and false positives. Comparing your institution’s performance against these benchmarks using a platform like Visbanking allows you to pinpoint whether an issue lies in front-line training, technology, or policy, thereby enabling targeted, resource-efficient improvements to your AML compliance checklist execution.
2. Pillar 2: Optimizing Your Suspicious Activity Reporting (SAR) System
Your Suspicious Activity Reporting (SAR) system is the critical conduit between your institution’s internal controls and national security. For executives, the focus must shift from simply filing SARs to optimizing the entire reporting lifecycle. An inefficient system—bogged down by false positives and slow investigations—not only fails to provide timely intelligence to law enforcement but also represents a significant operational cost and regulatory vulnerability.

The volume of SARs is staggering, with FinCEN receiving over 3.6 million in 2022 alone. This highlights the importance of quality over quantity. If your investigators spend 90% of their time clearing low-quality alerts, your institution is exposed. The goal is to benchmark your SAR metrics, such as the alert-to-SAR conversion rate and average investigation time, against peer institutions to identify whether your team is detecting genuine risk or chasing phantoms. For example, if your institution files 50 SARs per billion in assets while your peers average 25, the board must ask: are we twice as risky, or twice as inefficient?
Actionable Strategy: Intelligence-Led Reporting
A world-class SAR program is not a reactive function but a proactive, intelligence-led operation. It prioritizes the investigation of high-quality alerts that provide meaningful information to authorities. Following regulatory scrutiny, institutions like Standard Chartered have made substantial investments to improve their SAR processes, focusing on better data analytics and investigator training to enhance the quality of their filings.
To elevate your SAR system, your team must focus on these critical actions:
- Calibrate Monitoring Rules: Continuously tune your transaction monitoring scenarios based on historical SAR data and emerging typologies to reduce the volume of false positives, freeing up investigators for more complex cases.
- Establish Clear Timelines: Implement and enforce strict internal SLAs for the entire SAR lifecycle—from alert generation to investigation and final filing—ensuring you meet the 30-day regulatory deadline without fail.
- Enhance Investigator Training: Equip your team with ongoing training on the latest money laundering indicators and narrative writing techniques to ensure every SAR filed is clear, concise, and actionable for law enforcement.
- Implement Quality Assurance: Introduce a mandatory quality assurance (QA) review of all draft SARs before filing. This step catches errors, ensures completeness, and validates the decision-making process, strengthening a key component of your AML compliance checklist.
Benchmarking Key Performance Indicators
Tracking SAR-related metrics provides a direct line of sight into the efficiency and effectiveness of your financial crime detection capabilities. When your alert-to-SAR conversion rate is significantly lower than that of your peers, it signals a potential miscalibration of your monitoring system or a need for enhanced investigator training.
By leveraging a data intelligence platform, you can compare your SAR metrics against a curated peer group, transforming abstract compliance duties into measurable performance objectives. This allows you to justify investments in technology and training with hard data, demonstrating a commitment to building a more resilient and efficient defense against financial crime. For more information, you can explore our detailed guide on the Suspicious Activity Reporting (SAR) System on Visbanking.com.
3. Transaction Monitoring and Screening
If Customer Due Diligence is your first line of defense, your transaction monitoring system is the ever-vigilant sentry guarding the gates. For executives, the critical question is no longer "Do we monitor transactions?" but "How intelligent and efficient is our monitoring?" A system that generates thousands of low-quality alerts per week is not a safety net; it is an operational black hole, draining resources that could be better spent on genuine risk mitigation.

When an institution like Wells Fargo commits $3 billion to risk and compliance technology, it signals a fundamental shift. The goal is moving beyond legacy, rules-based systems to intelligent, adaptive monitoring. A high false positive rate is a direct tax on your profitability. If your false positive rate is 98% while peers with similar technology achieve 95%, that 3% difference represents millions in wasted labor annually. Benchmarking alert-to-SAR conversion rates and the average time to close an alert against peer institutions quantifies the cost of this inefficiency and builds a business case for system modernization.
Actionable Strategy: Calibrate for Precision
An effective transaction monitoring program is not about casting the widest possible net; it is about using the sharpest spear. The objective is to fine-tune your systems to detect genuinely anomalous behavior while minimizing the noise that overwhelms your investigation teams. ING's strategic adoption of machine learning to reduce false positives is a prime example of using technology to enhance, not just expand, compliance efforts.
To achieve this level of precision, your team must focus on these critical actions:
- Regularly Calibrate Monitoring Rules: Your rules are not static. They must be reviewed and adjusted based on new typologies, emerging risks, and the performance of the system itself. Document every change and the logic behind it for regulatory scrutiny.
- Integrate Machine Learning: Use machine learning models to analyze complex data sets and identify subtle patterns that rule-based systems miss. This approach dramatically improves detection accuracy and reduces false positives, freeing up your analysts.
- Test System Performance: Don't wait for a real event to discover a system weakness. Use synthetic data and scenario testing to proactively validate your system's effectiveness against known money laundering schemes.
- Ensure Adequate Staffing and Training: An advanced system is only as good as the team investigating its alerts. Your AML compliance checklist must include provisions for a well-trained, adequately staffed team capable of making sound, timely decisions.
4. Pillar 4: Architecting a Dynamic AML Risk Assessment Framework
An institution’s AML Risk Assessment is not a compliance formality; it is the strategic blueprint for your entire risk management architecture. For executives, the core question is whether this assessment is merely a static, check-the-box exercise or a dynamic tool that actively informs resource allocation and business strategy. An outdated or superficial risk assessment leads to misallocated capital, with teams either over-investing in low-risk areas or, more dangerously, under-resourcing high-risk vulnerabilities.
If your institution cannot quantify the risk exposure from a new digital payment product or a geographic expansion, your AML program is operating blind. This is where comprehensive data analysis becomes critical. Benchmarking your institution's risk profile—product mix, geographic footprint, and customer types—against peers allows you to see if your risk ratings are calibrated correctly or if you have a significant blind spot. For example, if your peer group shows a 15% higher exposure to high-risk geographies, it should prompt an immediate review of your own risk assessment assumptions.
Actionable Strategy: Enterprise-Wide Risk Integration
A truly effective AML Risk Assessment must be a living document, embedded across the organization. Its purpose is to systematically identify, measure, and mitigate money laundering and terrorist financing risks across all products, customer segments, and geographies. After facing regulatory scrutiny, institutions like Commonwealth Bank of Australia undertook significant enhancements to their risk assessment methodologies, ensuring they were more granular and responsive to emerging threats.
To transform your assessment from a static report to a strategic asset, focus on these critical actions:
- Involve Business Lines in Risk Identification: Collaborate directly with product owners and relationship managers. They possess frontline knowledge of customer behaviors and product use cases that is invaluable for identifying inherent risks.
- Use a Hybrid of Quantitative and Qualitative Data: Combine hard metrics like transaction volumes and geographic data with qualitative assessments from subject matter experts to create a holistic risk picture.
- Align Your Risk Appetite with Business Strategy: Ensure the board-approved risk appetite statement directly informs the risk assessment process. This alignment prevents a disconnect where business objectives inadvertently introduce unacceptable compliance risks.
- Document Everything: Meticulously document your methodology, assumptions, and control-testing results. This documentation is crucial for regulatory exams and for validating the assessment’s accuracy over time.
Benchmarking Key Performance Indicators
Tracking the effectiveness of your risk assessment goes beyond the assessment itself; it is reflected in the efficiency of your entire AML program. The following infographic highlights target KPIs for an institution with a well-calibrated risk framework.
These metrics indicate that risk-based controls are working as intended, focusing resources where they are most needed and minimizing unnecessary friction. By using a platform like Visbanking to compare your operational metrics against these benchmarks, you can validate the accuracy of your risk assessment. This data-driven approach allows you to confidently demonstrate to regulators and the board that your AML compliance checklist is built upon a sound, evidence-based foundation.
5. Pillar 5: Embedding a Culture of Compliance with an AML Training and Awareness Program
Your AML technology and policies are only as effective as the people who use them. For executives, the critical question is not whether employees complete training, but whether the training effectively alters behavior and strengthens your human firewall against financial crime. An inadequate program creates a false sense of security, leaving the institution vulnerable to breaches that sophisticated systems alone cannot prevent.
If your training program suffers from low engagement or fails to cover role-specific risks, you are creating a significant vulnerability. For instance, a relationship manager who doesn't understand the AML red flags specific to their high-net-worth clients can unknowingly facilitate illicit transactions. Institutions like Goldman Sachs and Barclays invest heavily in comprehensive, role-specific training modules because they recognize that a well-informed employee is the most critical line of defense in a robust AML compliance checklist.
Actionable Strategy: Role-Specific, Continuous Education
An effective training program moves beyond generic, once-a-year presentations. It must be dynamic, targeted, and ingrained in the daily workflow to build a true culture of compliance. The objective is to empower every employee, from the teller line to the executive suite, with the knowledge to identify and report suspicious activity confidently and correctly.
To achieve this, your organization must focus on these critical actions:
- Tailor Content to Job Functions: Develop specific training modules for different roles. A trade finance specialist needs different knowledge than a retail banking associate. Use real-world case studies relevant to their daily tasks.
- Implement Regular Testing and Certification: Move beyond simple completion metrics. Use regular assessments and certifications to ensure comprehension and retention of key AML principles and internal procedures.
- Track Effectiveness and Adapt: Monitor metrics such as the quality and volume of internal escalations of suspicious activity pre- and post-training. A spike in well-documented, relevant escalations from a specific department often indicates successful training.
- Keep Content Current: The regulatory and threat landscape is constantly evolving. Your training materials must be updated frequently to reflect new regulations, typologies, and emerging risks.
6. Independent AML Audit and Testing
An independent audit is the ultimate validation of your AML program's integrity and effectiveness. For executives, this is not a check-the-box exercise but a critical diagnostic tool. The key question is: “Does our independent testing provide an objective, unvarnished view of our control environment, or is it merely confirming existing biases?” An audit that fails to challenge the status quo provides a false sense of security, leaving the institution exposed to regulatory enforcement and reputational damage.
If your internal audit finds no significant issues year after year, yet a regulatory exam uncovers systemic weaknesses, there is a dangerous disconnect. This gap signifies a failure in audit scope, methodology, or independence. Major financial institutions like JPMorgan Chase use rigorous internal and external audit assessments to continuously validate their controls, using findings to drive programmatic improvements and demonstrate a proactive compliance posture to regulators.
Actionable Strategy: Proactive Validation and Remediation
A best-in-class audit function operates as a strategic partner to the business, not an adversary. Its purpose is to identify vulnerabilities before they escalate into crises. The goal is to create a continuous feedback loop where testing informs remediation, and remediation strengthens controls, thereby enhancing the overall resilience of your AML compliance checklist.
To ensure your audit function delivers maximum value, your team should focus on these critical actions:
- Develop a Risk-Based Audit Plan: Focus audit resources on high-risk areas identified through your enterprise-wide risk assessment, such as new products, high-risk geographies, or areas with previously identified control weaknesses.
- Ensure Auditor Expertise: Whether using internal staff or external firms like KPMG, verify that auditors possess deep, current expertise in AML regulations and financial crime typologies. A generalist approach is insufficient for a specialized field.
- Implement Robust Remediation Tracking: Establish a formal, centralized system to track audit findings, assign ownership for corrective actions, and monitor progress against deadlines. This ensures accountability and prevents issues from recurring.
- Maintain Open Communication: Foster a culture of transparency where audit findings are communicated clearly and regularly to senior management and the Board's audit committee, enabling informed oversight and strategic decision-making.
7. Pillar 7: Mastering Sanctions Compliance and Screening
A failure in sanctions compliance is not just a regulatory misstep; it is a catastrophic business risk that can erase billions in value overnight. For executives, the core concern is whether their screening systems are robust enough to detect and block prohibited transactions in real-time. The consequences, as seen in the landmark $8.9 billion settlement paid by BNP Paribas for processing transactions involving sanctioned entities, are an existential threat to an institution's capital and reputation.
Effective sanctions screening goes beyond simply subscribing to an Office of Foreign Assets Control (OFAC) list. It demands a dynamic, multi-layered defense system capable of screening customers, counterparties, and transactions across all business lines against an ever-changing global landscape of restrictions from the UN, EU, and other authorities. If your screening system flags thousands of false positives daily, you are not just incurring operational costs; you are creating noise that could mask a genuine, high-stakes violation.
Actionable Strategy: Dynamic and Comprehensive Screening
The goal is to build a screening ecosystem that is both comprehensive in its coverage and intelligent in its application, minimizing false positives while ensuring no illicit transaction slips through. This requires a fusion of technology, data integrity, and human expertise. Following its own sanctions-related penalties, Standard Chartered invested heavily in technology and personnel to create a more sophisticated, risk-based screening framework, demonstrating the commitment required to remediate such critical failures.
To build a world-class sanctions screening program, focus on these critical actions:
- Implement Comprehensive Screening: Ensure your screening technology is integrated at all key touchpoints: customer onboarding (KYC), transaction processing, and periodic reviews. This creates multiple nets to catch potential violations.
- Maintain Current Data Feeds: Your sanctions lists are only as good as they are current. Automate daily updates from all relevant authorities (OFAC, UN, EU, HM Treasury) to ensure your screening logic is based on the latest intelligence.
- Document Every Decision: Every alert, whether cleared or escalated, must have a clear, documented rationale. This audit trail is indispensable for demonstrating programmatic rigor to regulators during an examination. A well-defined AML compliance checklist should include a protocol for this documentation.
Benchmarking Key Performance Indicators
To gauge the efficiency and effectiveness of your sanctions program, you must track relevant KPIs. A high false positive rate could indicate that your screening rules are too broad or your customer data is poor, leading to wasted resources. Conversely, a zero-hit rate might suggest a system that is not functioning correctly at all.
Comparing metrics like alert-to-investigation ratios and the average time to resolve an alert against industry benchmarks provides a clear, data-driven view of your program's health. By using a platform like Visbanking to analyze these KPIs against peer institutions, executives can move from reactive problem-solving to proactive, strategic optimization of their sanctions compliance framework.
7-Point AML Compliance Comparison
| Item | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Customer Due Diligence (CDD) Program | High – multi-step verification, ongoing reviews | High – tech investment, trained staff | Strong customer risk profiles, reduced ML risk | Onboarding & ongoing risk management | Comprehensive risk-based approach, regulatory protection |
| Suspicious Activity Reporting (SAR) System | Medium – monitoring plus investigative workflow | High – investigation teams, case management | Timely, accurate reporting to authorities | Detecting and reporting suspicious financial acts | Regulatory compliance, legal safe harbor protection |
| Transaction Monitoring and Screening | High – real-time analytics, AI/ML integration | High – technology, calibrated rules | Early suspicious pattern detection, scalable | Automated transaction analysis for AML/Sanctions | Broad transaction coverage, efficient detection |
| AML Risk Assessment Framework | Medium-High – data analysis, risk modeling | Medium – analytical expertise, business input | Strategic risk-based compliance, resource allocation | Institution-wide AML risk prioritization | Optimizes controls and resources, supports strategy |
| AML Training and Awareness Program | Medium – content development, ongoing delivery | Medium – training resources, time investment | Educated staff, reduced operational risks | Compliance culture building across organization | Enhances employee vigilance, supports regulatory req. |
| Independent AML Audit and Testing | Medium – audit planning, comprehensive testing | High – specialized auditors, resource heavy | Objective program effectiveness validation | Program quality assurance, regulatory examination | Identifies gaps, promotes continuous improvement |
| Sanctions Compliance and Screening | High – real-time screening, list updates | High – systems, frequent updates, training | Prevents sanctions violations, avoids penalties | Cross-border transactions, sanctions-sensitive sectors | Protects against sanctions risks, supports compliance |
From Checklist to Competitive Advantage: The Future of AML Compliance
Navigating this comprehensive AML compliance checklist reveals a fundamental shift in the financial industry. Compliance is no longer a reactive, box-ticking exercise confined to a specific department; it is a strategic, enterprise-wide imperative driven by data, technology, and a forward-looking view of risk management. The seven pillars we have detailed are not isolated controls but interconnected components of a dynamic defense system. Their collective strength is realized only when measured, managed, and optimized through sophisticated data intelligence.
For banking executives and board members, the critical question has transcended "Are we compliant?" The more telling inquiries are now:
- How does our compliance performance benchmark against our peers? Are our SAR filing rates significantly higher or lower than banks of a similar size and risk profile? A significant deviation in either direction demands investigation.
- Where are the hidden risks and operational inefficiencies in our program? Are we over-investing in low-risk areas while under-resourcing high-risk ones?
- Is our technology stack delivering a measurable return on investment? How do our transaction monitoring alert volumes and false-positive rates compare to the industry standard?
A passive stance, where an institution waits for an MRA (Matter Requiring Attention) from an examiner or a critical finding from an independent audit, is a strategy laden with unnecessary risk. This reactive posture not only invites regulatory scrutiny and potential penalties but also cedes a significant competitive advantage to more proactive institutions.
Transforming Compliance from Cost Center to Strategic Asset
The true power of mastering your AML program lies in moving from a defensive crouch to a data-informed strategy. When you continuously benchmark your programs, staffing levels, and technology investments against a precisely defined peer group, you transform compliance from a perceived cost center into a source of institutional resilience and market differentiation.
Consider a scenario where a bank's internal review shows its AML-related staffing costs are 25% higher than the average for its asset size. Without external data, this might be justified as a conservative investment in safety. However, with peer benchmarking data from a platform like Visbanking, the bank might discover its SAR filing volume is only average, and its false positive rate on transaction alerts is 40% higher than its peers. This insight reframes the conversation. The problem is not overspending but inefficiency, likely rooted in outdated monitoring systems or inadequate model tuning. The data provides a clear, actionable path: invest in technology modernization to reduce manual review and improve accuracy, ultimately lowering costs while strengthening compliance.
This data-driven approach fosters a culture of continuous improvement and strategic foresight. It allows leadership to allocate resources with precision, justify technology investments to the board with concrete data, and demonstrate a sophisticated, risk-based approach to regulators. In an increasingly complex global financial system, the banks that thrive will be those that harness the power of data to not only meet their AML compliance checklist obligations but to turn them into a clear competitive advantage.
Ready to move from defense to offense? The Visbanking Bank Intelligence and Action System provides the peer analytics and market intelligence you need to benchmark your AML program's performance and identify strategic opportunities. Explore how Visbanking can help your institution transform compliance from an obligation into an advantage.